We are thrilled to announce the upcoming release of ai.virtuallyaware.com. We will explore the AI phenomenon from both an evaluative and technical perspective, while highlighting its common use cases that will empower IT professionals like never before.
Evaluating
We are all new to AI as it emerges and matures. On this site we share what we discover. All the good or bad and how it might fit into your different business units.
Common Use Cases for IT Professionals
The possibilities for leveraging AI in the realm of IT are immense. We will explore some key use cases where the impact of AI is expected to be particularly transformative:
1. Data Analysis and Insights
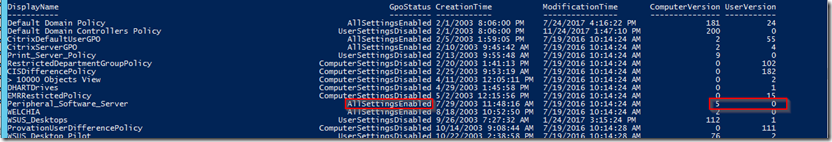
AI can revolutionize data analysis by providing advanced insights and predictions. IT professionals can harness AI to process large volumes of data at an unprecedented speed, identify patterns, and generate valuable insights that can drive informed decision-making.
2. Cybersecurity
In the era of increasing cybersecurity threats, AI can be a potent weapon in an IT professional’s arsenal. AI-powered systems can analyze vast amounts of data to detect anomalies, identify potential security breaches, and proactively respond to threats in real-time.
3. IT Efficiency
Managing and optimizing diverse IT environments can be challenging. From day to day tasks, to script building, to building automated processes in conjunction with other IT tools, the efficiencies that can be achieved are career changing.
4. And More….
Psychology of the AI Revolution
Just as virtualization and cloud technologies revolutionizing IT, the advent of AI marks a paradigm shift in the way IT professionals work. This will also require a new way of thinking and decision making far beyond the IT professional. Just as virtualization and cloud technologies had psychological barriers long after they were technically sound, AI will face the same skepticism and fear. Hopefully here we can alleviate some of that as we share our experiences through the evaluative prowess, technical brilliance, and a plethora of use cases AI promises. Stay tuned for updates on its release, as we prepare to embrace this transformative technology.
We would love to hear your thoughts and expectations on the upcoming AI revolution. Share your insights in the comments below and let us embark on this journey together!